Couple of personal words …
Dear Readers! In the past I posted posts related to the application security and Keycloak.
I have learned Istio recently and I will happy to share my knowledge.
You will continue to see my Keycloak posts, but you will also enjoy form my DevSecOps posts.
Stay tuned!
What will I cover in the post?
You will understand what is is Istio and then You will deploy a simple demo that show how to use Istio.
What is a service mesh?
Let’s first understand what is a service mesh. A service mesh is an infrastructure layer for making service-to-service communication safe, fast and reliable.
The service mesh allows to add additional capabilities to a micro-services deployment:
- traffic control
- failure recovery
- service discovery
- load balancing
- observability
- security
What is Istio?
Istio is an implementation of a service mesh. Istion is open-source software and created as a collaboration of Google, IBM and Lyft.
Istio provides the very good documentation and I will refer to it during my posts.
Istio Simple Demo
The show time!
During my posts I will use Google Kubernetes Engine (GKE).
The Istio installation is very simple: you just need to select “Enable Istio” during the creation of your GKE cluster.
Istio Bookinfo Demo deployment
The Istio Bookinfo Demo is described here.
Istio automatic sidecar proxy injection
Let’s first configure Istio’s automatic sidecar proxy injection:
kubectl label namespace default istio-injection=enabled
You will see the following output shows the command completed successfully:
namespace/default labeled
Demo deployment
Now, let’s deploy the demo application:
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.2/samples/bookinfo/platform/kube/bookinfo.yaml
The output shows that the application is deployed successfully:
service/details created
serviceaccount/bookinfo-details created
deployment.apps/details-v1 created
service/ratings created
serviceaccount/bookinfo-ratings created
deployment.apps/ratings-v1 created
service/reviews created
serviceaccount/bookinfo-reviews created
deployment.apps/reviews-v1 created
deployment.apps/reviews-v2 created
deployment.apps/reviews-v3 created
service/productpage created
serviceaccount/bookinfo-productpage created
deployment.apps/productpage-v1 created
Demo pods
If we will check the containers deployed in each pod we will see that we have the Istio sidecar proxy deployed in each pod attached to each container:
kubectl get pods --namespace default -o=jsonpath='{range .items[*]}{"\n"}{.metadata.name}{":\t"}{range .spec.containers[*]}{.image}{", "}{end}{end}' |\
sort
In our case the list shows the gke.gcr.io/istio/proxyv2:1.1.13-gke.0 proxy:
details-v1-68fbb76fc-5ncg4: docker.io/istio/examples-bookinfo-details-v1:1.15.0, gke.gcr.io/istio/proxyv2:1.1.13-gke.0,
productpage-v1-6c6c87ffff-jmrs8: docker.io/istio/examples-bookinfo-productpage-v1:1.15.0, gke.gcr.io/istio/proxyv2:1.1.13-gke.0,
ratings-v1-7bdfd65ccc-ttkcx: docker.io/istio/examples-bookinfo-ratings-v1:1.15.0, gke.gcr.io/istio/proxyv2:1.1.13-gke.0,
reviews-v1-5c5b7b9f8d-klkk2: docker.io/istio/examples-bookinfo-reviews-v1:1.15.0, gke.gcr.io/istio/proxyv2:1.1.13-gke.0,
reviews-v2-569796655b-d9k65: docker.io/istio/examples-bookinfo-reviews-v2:1.15.0, gke.gcr.io/istio/proxyv2:1.1.13-gke.0,
reviews-v3-844bc59d88-lhtld: docker.io/istio/examples-bookinfo-reviews-v3:1.15.0, gke.gcr.io/istio/proxyv2:1.1.13-gke.0,
Ensure internal access
Run the following command to ensure that the demo application is running:
kubectl exec -it $(kubectl get pod -l app=ratings -o jsonpath='{.items[0].metadata.name}') -c ratings -- curl productpage:9080/productpage | grep -o "<title>.*</title>"
You will see the following output:
<title>Simple Bookstore App</title>
Deploy the ingress gateway
Run the following command to deploy the Istio ingress gateway:
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.2/samples/bookinfo/networking/bookinfo-gateway.yaml
You will see the following output shows the gateway is deployed successfully:
gateway.networking.istio.io/bookinfo-gateway created
virtualservice.networking.istio.io/bookinfo created
Export ingress IP and port and ensure the internal access
Export ingress IP and port:
export INGRESS_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
export INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http2")].port}')
export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT
Access using external URL:
curl -s http://${GATEWAY_URL}/productpage | grep -o "<title>.*</title>"
The output is the same as previous, but you access using the external URL:
`
<title>Simple Bookstore App</title>
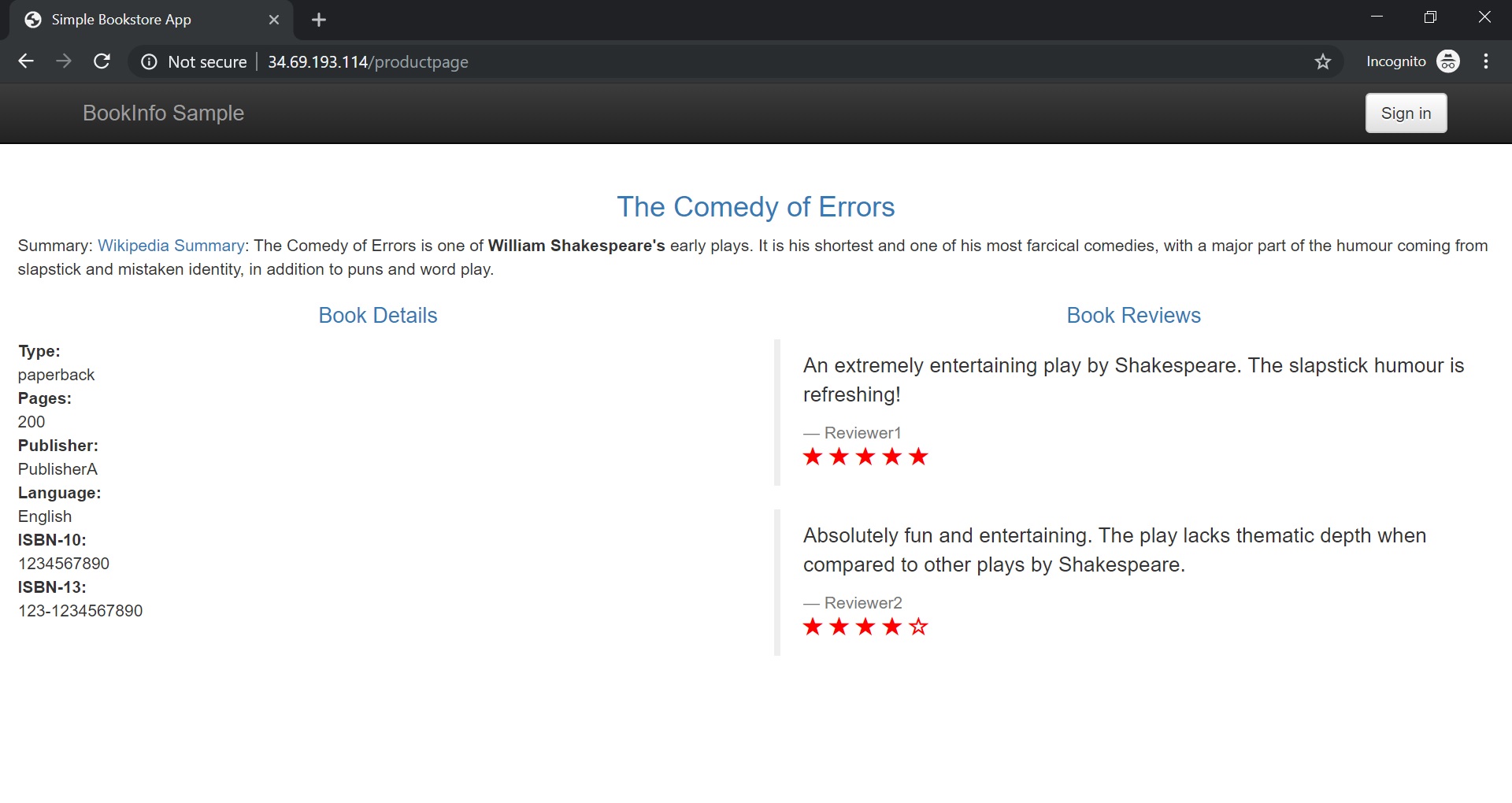
Access to the external URL from a browser
Now we will open the external URL http://${GATEWAY_URL}/productpage in a browser.
And we did it! It works from any browser in a world!
Take Aways
You can take the following take aways from the post:
First of all, you understand what is Istio. Second, to use Istio features you need to deply the Istio sidecar proxy in each pod. Last but not least, you can easy open a web application to to internal access using Istio ingress gateway.