Update Keycloak User Attributes from Okta SAML Provider
The post describes how to configure Keycloak and Okta to update Keycloak User Attributes from the Okta SAML Provider
Do not forget to follow me on Twitter
Why the User Attributes are empty?
In my previous post I have described how to configure the Okta SAML Provider.
You may be wondering and want to ask me the question: “Michael, why the User Attributes are empty? I have values in Okta but the in Keycloak values are empty.”
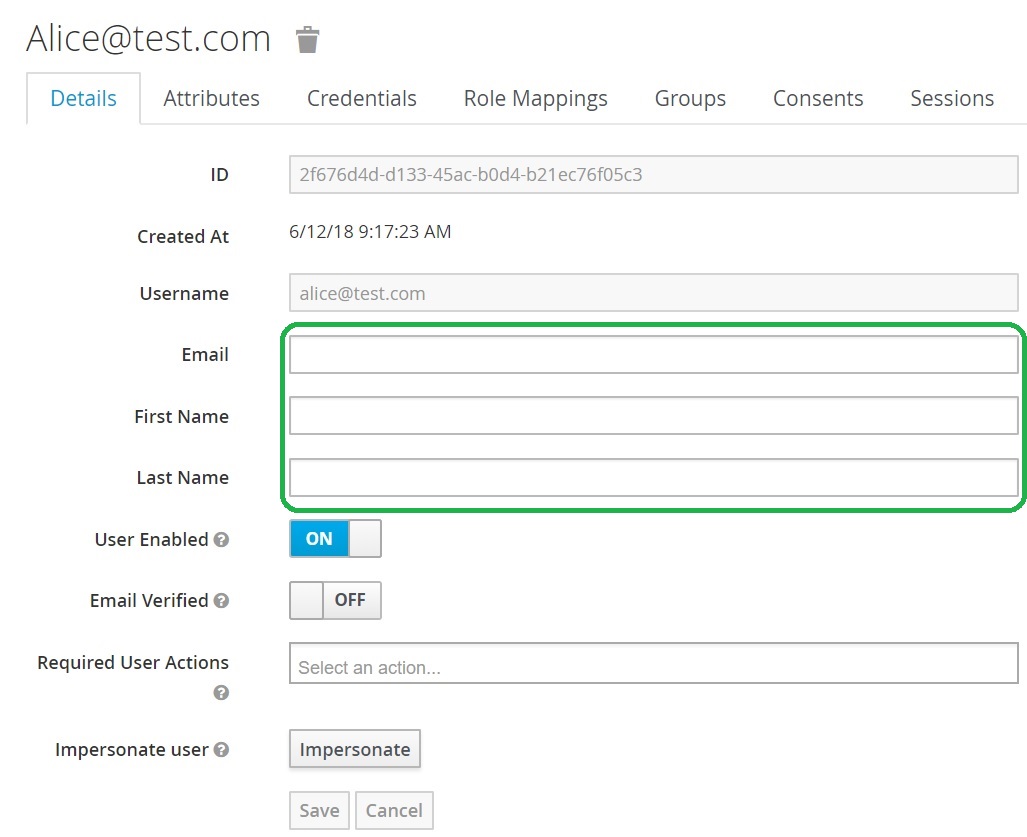
The answer is simple: You need to configure Okta to add the User Attributes to the SAML assertion and then you need to configure Keycloak to add these Attributes to the user.
Let’s do this.
Okta configuration
In the SAML Settings page of your SAML application locate the Attributes Statements (Optional) area.
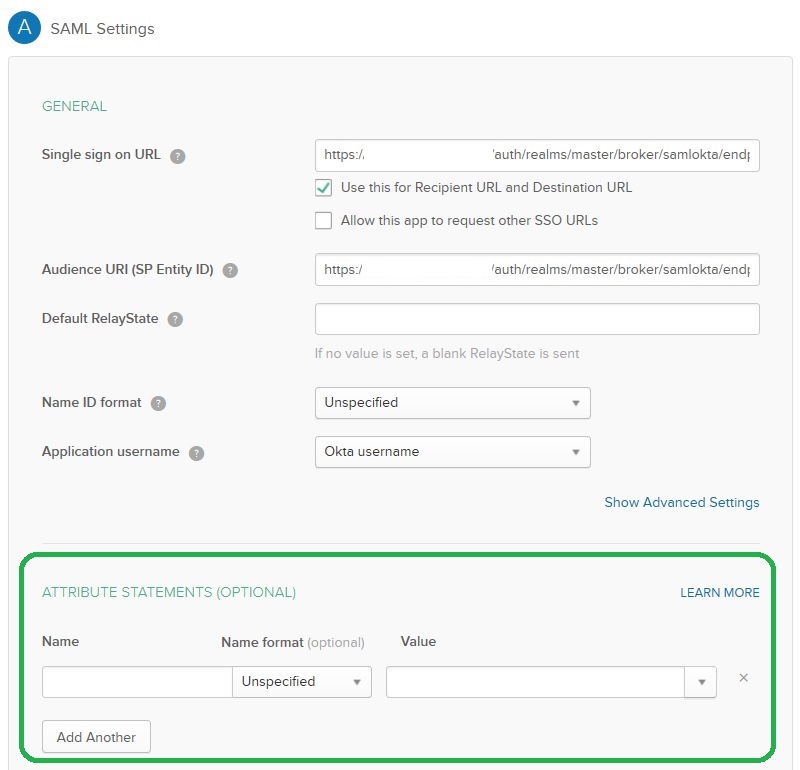
Select user.firstName from the Value list:
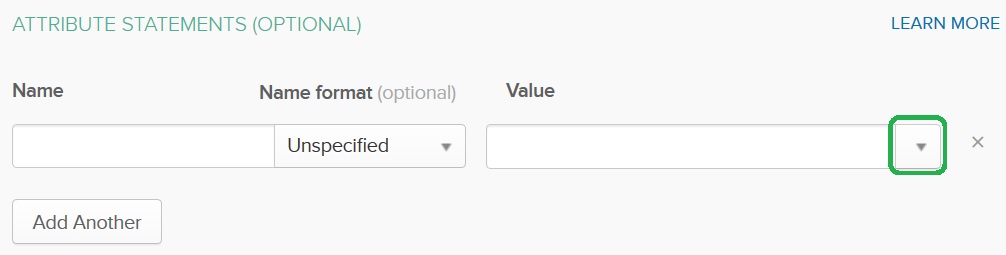
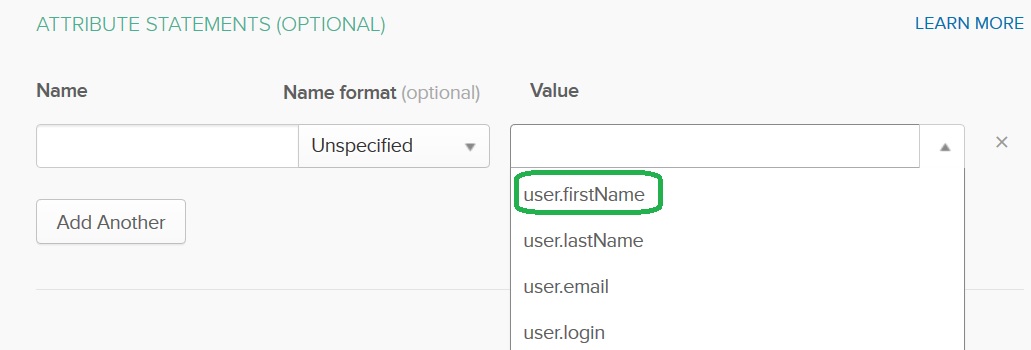
Provide the firstName Name and press on the Add Another button:
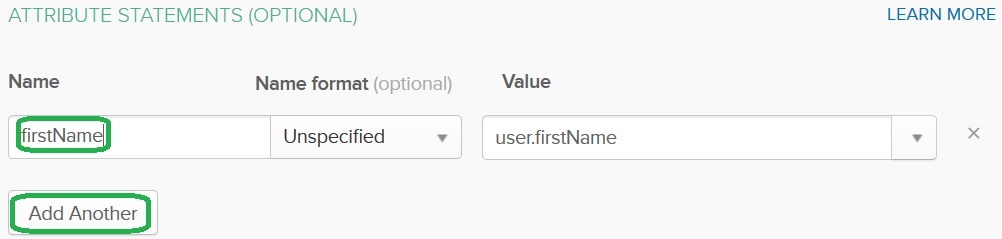
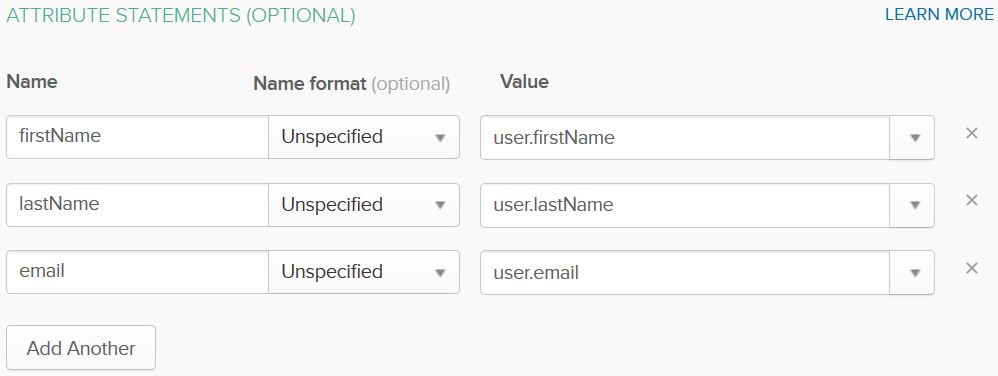
Add lastName from the user.lastName value and email from the user.email value and save the configuration. (Click Next and then click Finish.)
Keycloak configuration
Open the Keycloak admin page. From the menu click Identity Providers, select your SAML provider from the list of configured providers, open the Mappers tab and click Create.
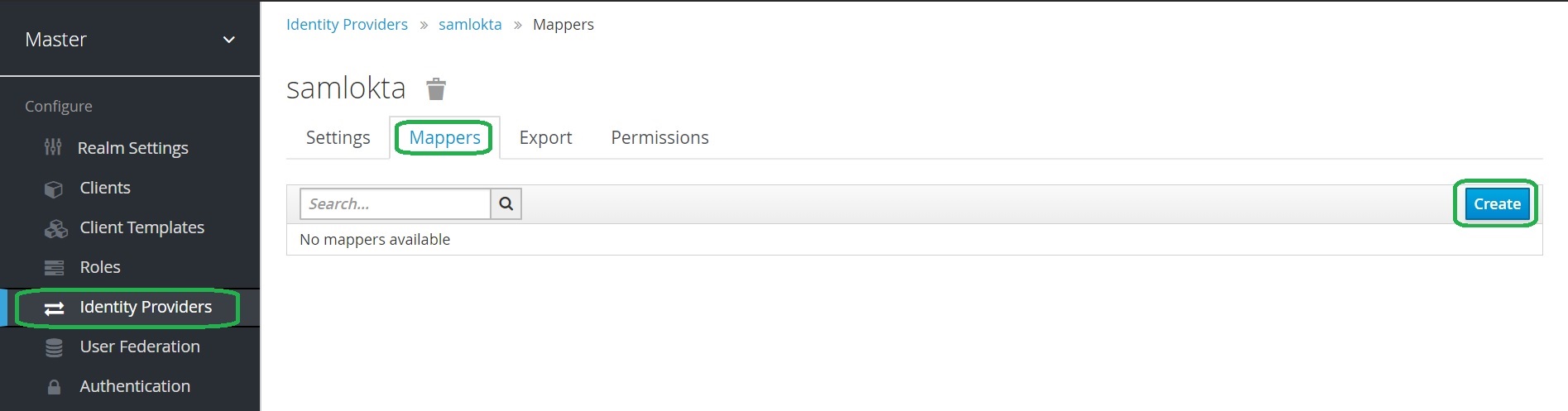
Select the Mapper Type Attribute Importer.
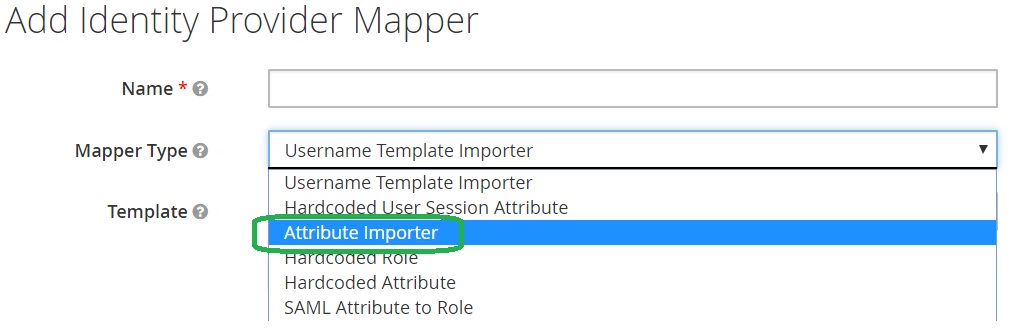
Complete the fields as follows: firstName for Name, Attribute Name, Friendly Name and User Attribute Name.
Click Save.
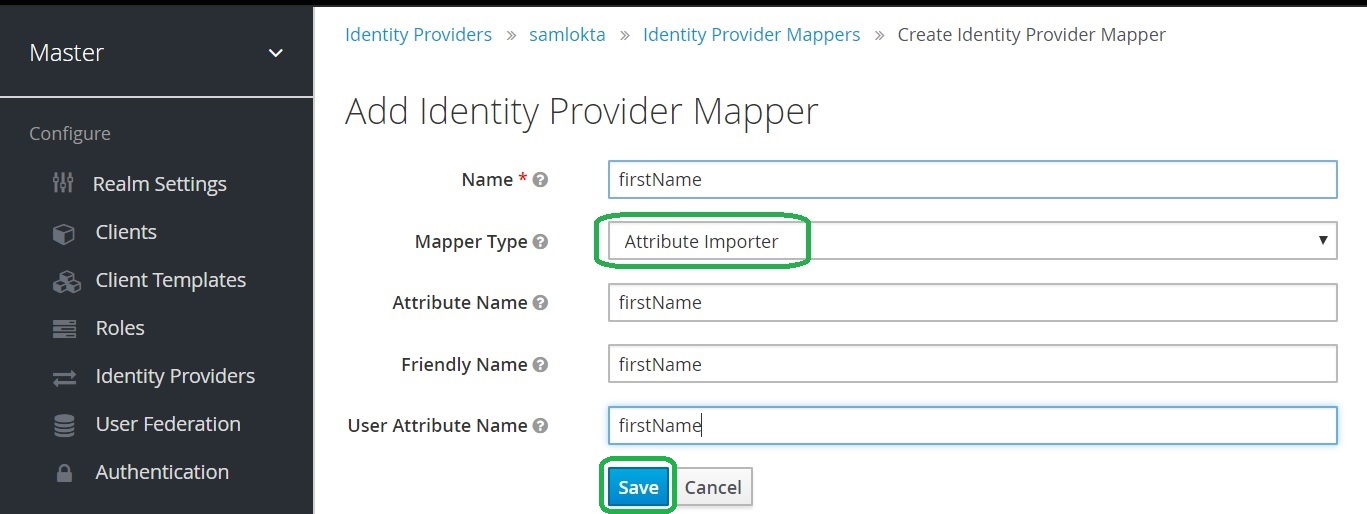
Note: Attribute Name is the name of the SAML attribute configured in the Okta application. The User Attribute Name is the Keycloak user attribute name.
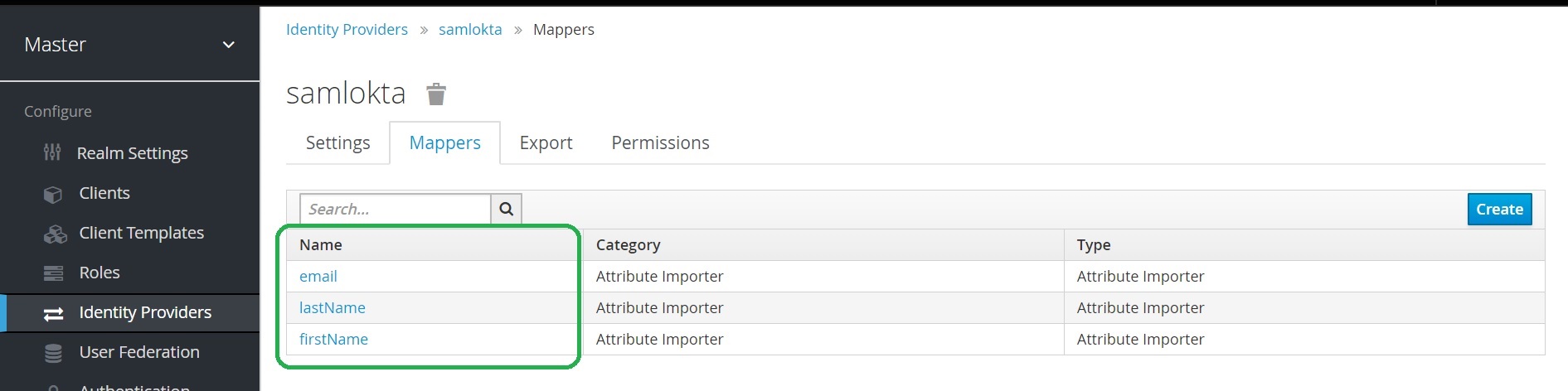
Repeat steps to add a mapper for lastName and email as you did for firstName. Below is an example of the how the mappers should look after they are configured.
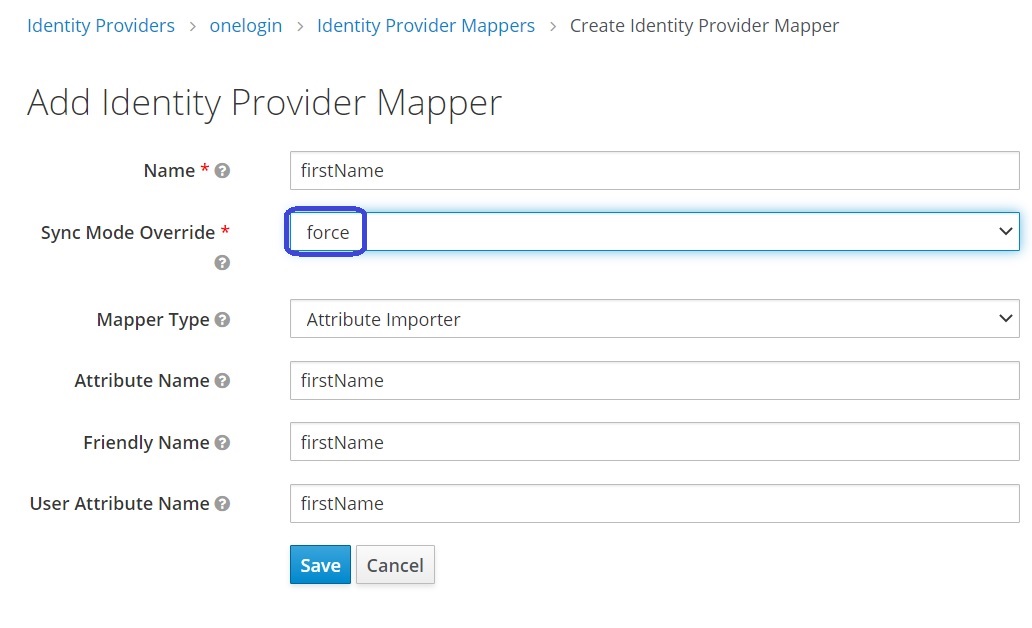
Keycloak v12 update
Important: Keycloak v12 supports the additional Sync Mode Override setting. Configure the setting to the force value. It will allow to update the user attribute during every login.
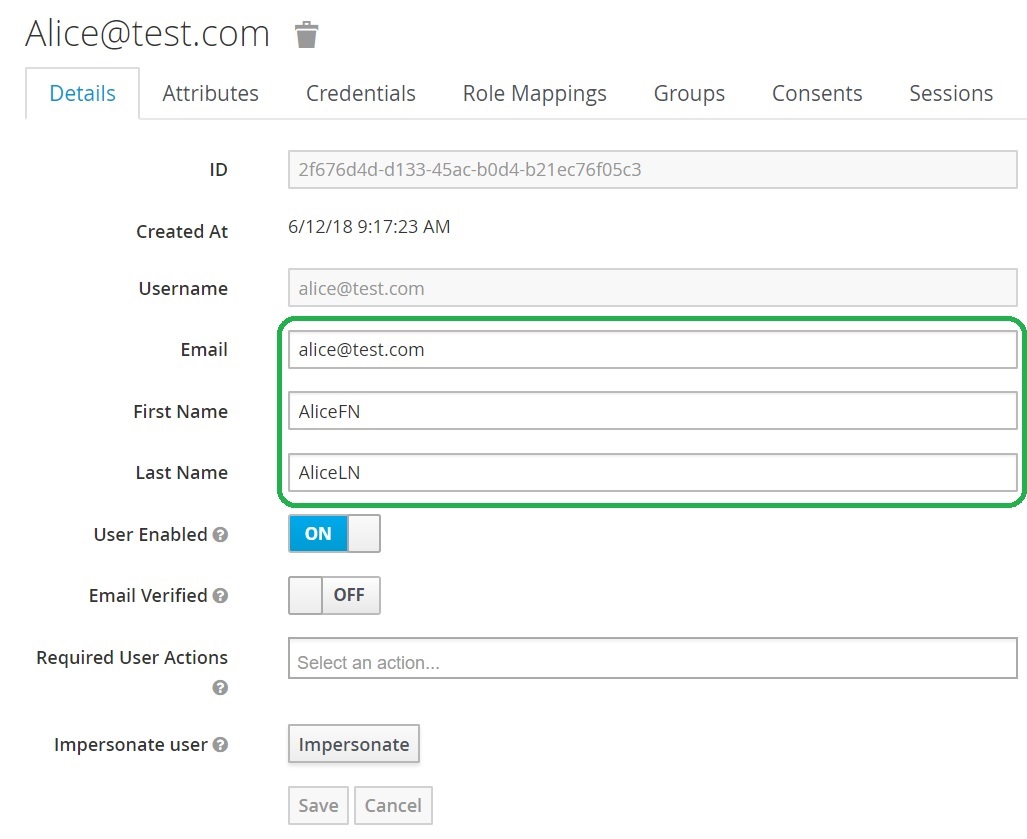
The User Attributes are full
The magic is happens, and the User Attributes are full after Okta authentication: