What will I cover in this post?
We will learn how to configure a WireGuard Virtual Private Network (VPN) for secure communication between two servers.
In this post, I plan on:
- Explaining what is WireGuard
- Explaining how to to configure WireGuard
What is WireGuard?
According to the WireGuard site:
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography.
WireGuard communicates via a WireGuard interface. You need to add the interface on both sides. WireGuard provides communication over UDP only.
How to to configure WireGuard?
Download WireGuard
Download WireGuard according to the site instructions to two servers.
Select a UDP port and IPs for the communication
Let’s select the UDP port for the communication between two servers.
The port should not be blocked by firewalls in your organization.
We will use the 51888 port the the post example.
Let’s select the IPs for the communication.
We will use 10.0.0.1 and 10.0.0.2 as depicted in the diagram:
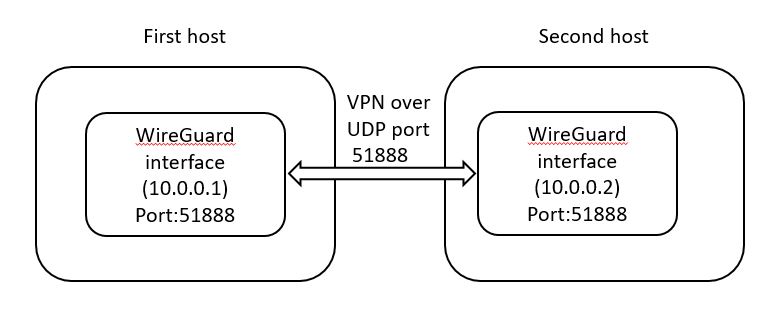
WireGuard setup
WireGuard quickstart provides the very good video. The commands below based on the video with comments.
Repeat these commands both on the first and the second hosts.
Create private and public keys
Create private and public keys:
wg genkey > private1
wg pubkey < private1
Setup the WireGuard interface
Create the WireGuard interface:
ip link add dev wg0 type wireguard
On the first host add the following IP to the interface:
ip address add 10.0.0.1/24 dev wg0
On the second host add the following IP to the interface:
ip address add 10.0.0.2/24 dev wg0
Add the private key to the interface. If you will not configure listen-port the port will be configured randomly:
wg set wg0 private-key ./private1 listen-port 51888
Start the interface:
ip link set wg0 up
Test the WireGuard interfaces
Test the WireGuard interface using command wg (equals to wg show).
On the first host:
interface: wg0
public key: PN9vLhCmGMVzuwUaBVSq0g4E8MACx5Hf73HT5AUiPgw=
private key: (hidden)
listening port: 51888
On the second host:
interface: wg0
public key: V4eNKGHy4sqV6sxYjoAvzwTMfDIs5yqaRQU7bhK0ERI=
private key: (hidden)
listening port: 51888
Mistake? Delete the WireGuard interface
During your tests you may delete the WireGuard interface using the following command:
ip link del dev wg1
Set the VPN peer
On the first host:
- Copy the second public key and configure it in the
peerattribute - Copy the second interface IP and configure it in the
allowed-ipsattribute - Copy the second host IP and configure it in the
endpointattribute
wg set wg0 \
peer V4eNKGHy4sqV6sxYjoAvzwTMfDIs5yqaRQU7bhK0ERI= \
allowed-ips 10.0.0.2/32 \
endpoint <second host IP>:51888
On the second host:
- Copy the first public key and configure it in the
peerattribute - Copy the first interface IP and configure it in the
allowed-ipsattribute - Copy the first host IP and configure it in the
endpointattribute
wg set wg0 \
peer PN9vLhCmGMVzuwUaBVSq0g4E8MACx5Hf73HT5AUiPgw= \
allowed-ips 10.0.0.1/32 \
endpoint <first host IP>:51888
Test the VPN peers
Let’s execute once again the command wg.
On the first host:
interface: wg0
public key: PN9vLhCmGMVzuwUaBVSq0g4E8MACx5Hf73HT5AUiPgw=
private key: (hidden)
listening port: 51888
peer: V4eNKGHy4sqV6sxYjoAvzwTMfDIs5yqaRQU7bhK0ERI=
endpoint: <second host IP>:51888
allowed ips: 10.0.0.2/32
On the second host:
interface: wg0
public key: V4eNKGHy4sqV6sxYjoAvzwTMfDIs5yqaRQU7bhK0ERI=
private key: (hidden)
listening port: 51888
peer: PN9vLhCmGMVzuwUaBVSq0g4E8MACx5Hf73HT5AUiPgw=
endpoint: <first host IP>:51888
allowed ips: 10.0.0.1/32
Test communication
On the first host
ping 10.0.0.2
PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data.
64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=2.24 ms
64 bytes from 10.0.0.2: icmp_seq=2 ttl=64 time=0.565 ms
64 bytes from 10.0.0.2: icmp_seq=3 ttl=64 time=0.665 ms
On the second host
ping 10.0.0.1
PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data.
64 bytes from 10.0.0.1: icmp_seq=1 ttl=64 time=0.894 ms
64 bytes from 10.0.0.1: icmp_seq=2 ttl=64 time=0.911 ms
64 bytes from 10.0.0.1: icmp_seq=3 ttl=64 time=0.496 ms
Test the handshake status
Let’s execute once again the command wg.
On the first host:
interface: wg0
public key: PN9vLhCmGMVzuwUaBVSq0g4E8MACx5Hf73HT5AUiPgw=
private key: (hidden)
listening port: 51888
peer: V4eNKGHy4sqV6sxYjoAvzwTMfDIs5yqaRQU7bhK0ERI=
endpoint: <second host IP>:51888
allowed ips: 10.0.0.2/32
latest handshake: 1 minute, 50 seconds ago
transfer: 1.25 KiB received, 1.30 KiB sent
On the second host:
interface: wg0
public key: V4eNKGHy4sqV6sxYjoAvzwTMfDIs5yqaRQU7bhK0ERI=
private key: (hidden)
listening port: 51888
peer: PN9vLhCmGMVzuwUaBVSq0g4E8MACx5Hf73HT5AUiPgw=
endpoint: <first host IP>:51888
allowed ips: 10.0.0.1/32
latest handshake: 1 minute, 46 seconds ago
transfer: 1.30 KiB received, 1.25 KiB sent
Congratulations!
Congratulations! You successfully connected two hosts using VPN!
Take-aways
You should now have a knowledge of what is WireGuard and how to configure it.