What will I cover in this post?
We will learn how to integrate Keycloak with Onelogin SAML Provider.
Do not forget to follow me on Twitter
Configuration
In my previous post I have described how to integrate Keycloak with Okta SAML Provider. The configuration with with Onelogin SAML Provider is very similar.
Keycloak and Onelogin need to be configured in parallel.
First, you need to add the SAML identity provider in Keycloak.
Then you to add a SAML application in Onelogin using the Keycloak Redirect URI value.
Finally, you need to import the Onelogin SAML application metadata into the Keycloak Identity Provider.
Add SAML identity provider in Keycloak
Open Keycloak admin page, click Identity Providers and select SAML v2.0 provider from the list of providers.
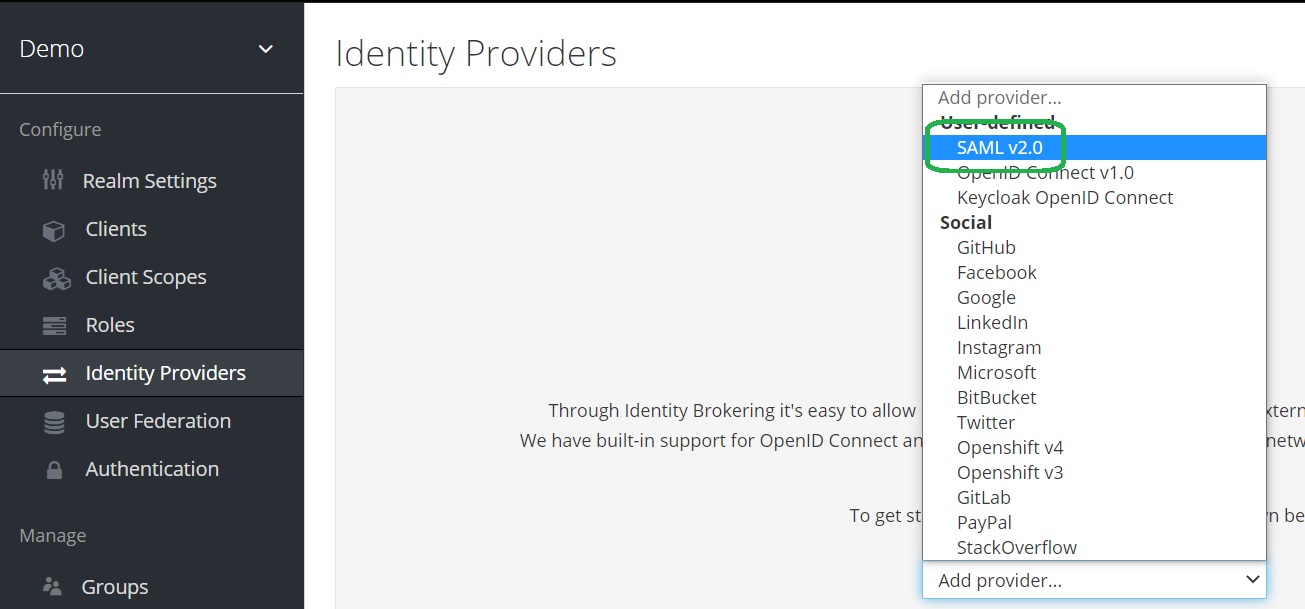
Keycloak SAML Identity Providers documentation is here
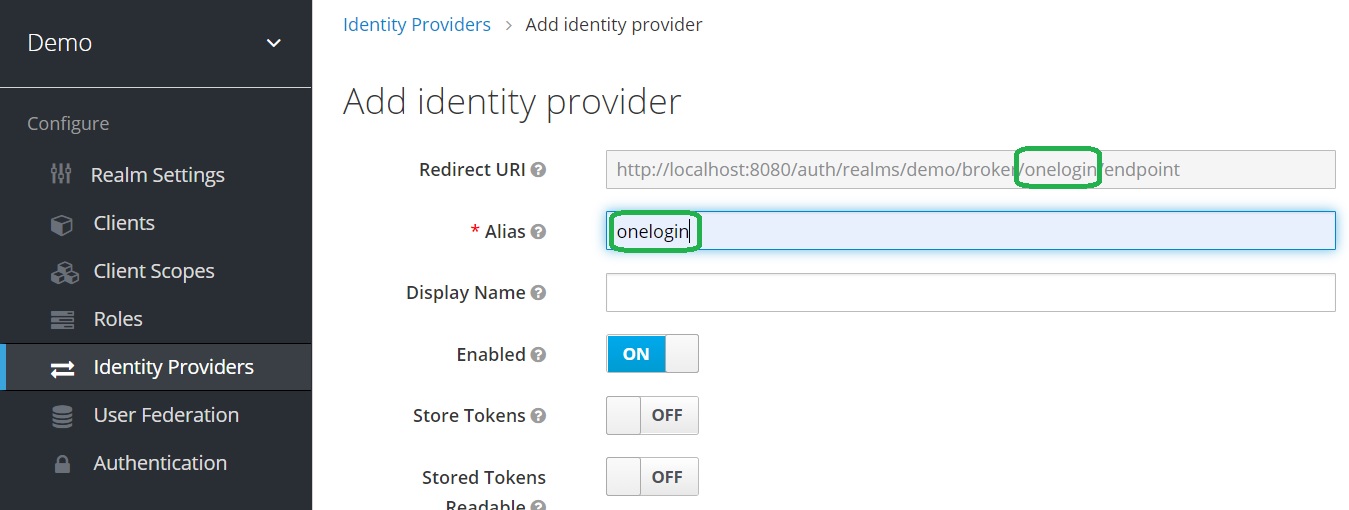
Configure SAML provider in Keycloak
Enter the Alias. Notice that it is part of Redirect URI.
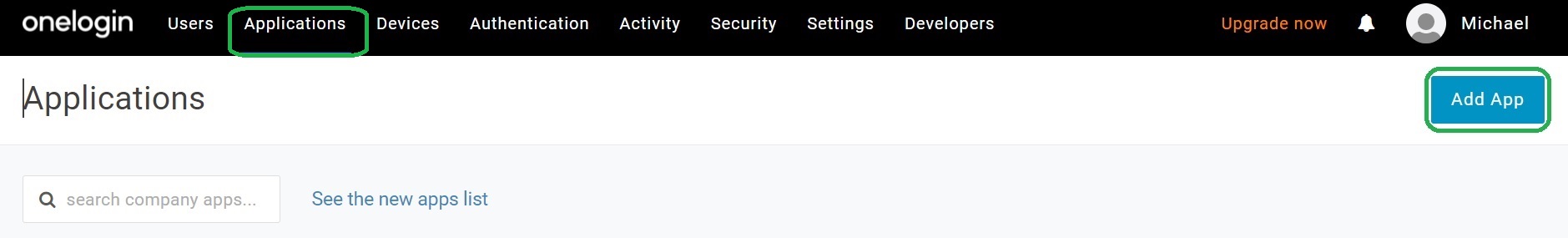
Add SAML application in Onelogin
Click on the applications in the menu and then click on the Add App button.
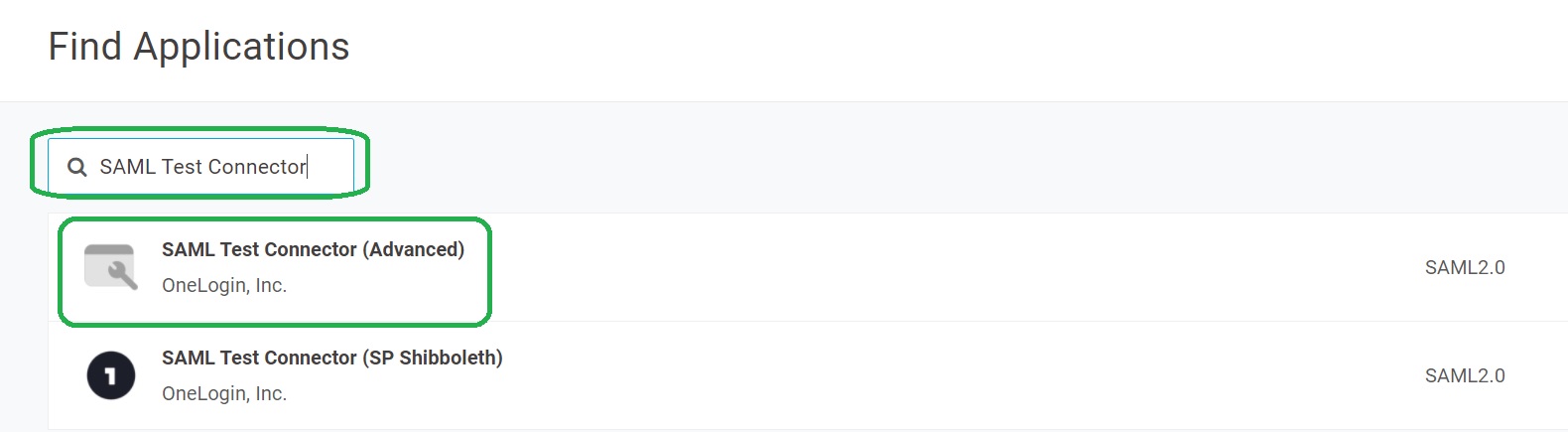
Find the SAML application
Type SAML Test Connector in the find control. Click on SAML Test Connector (advanced).
Provide the application name
Enter SAML Test Connector Demo and click Save.
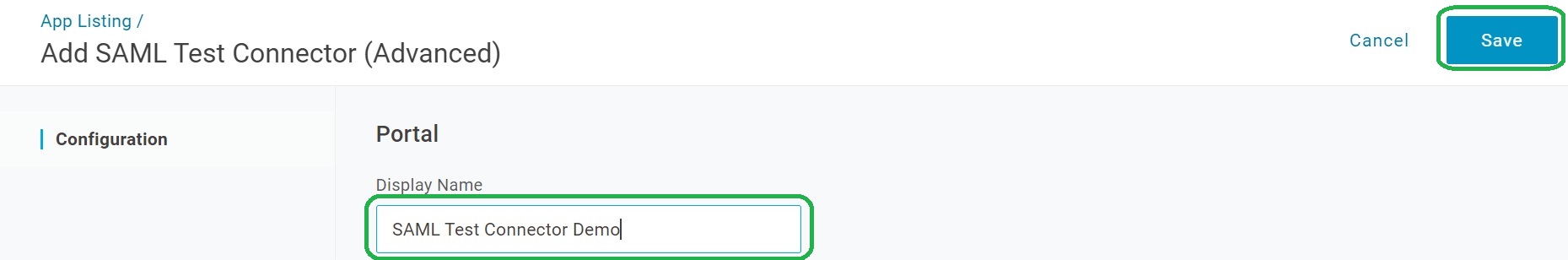
Configure SAML Settings
Open the Configuration tab.
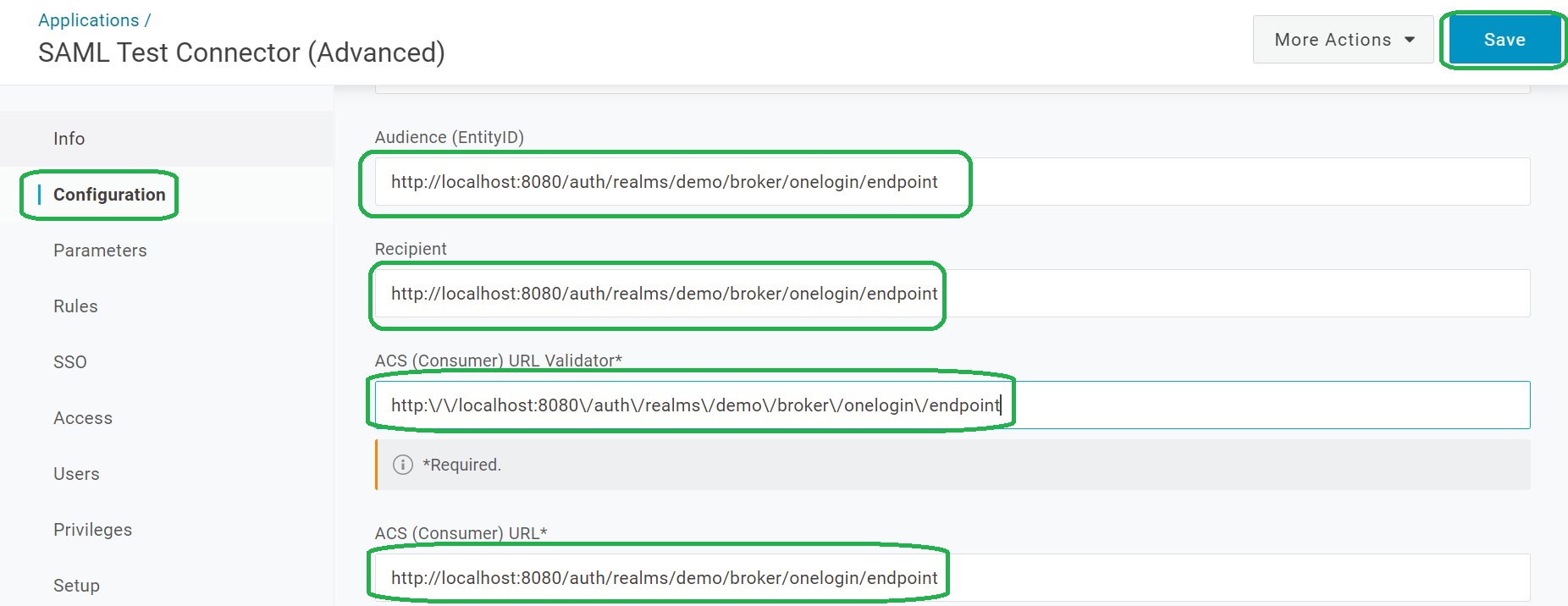
Configure SAML Settings by copying the Keycloak’s Redirect URI from the SAML v2.0 provider page of Keycloak to Audience (EntityID), Recipient and ACS (Consumer) URL settings.
Create the ACS (Consumer) URL Validator setting by adding a backslash for each slash in the Redirect URI.
Click Save.
Possible to use the value .* for the ACS (Consumer) URL Validator setting in a development environment.
The value will accept all URLs. It is not recommended to use the value in a production.
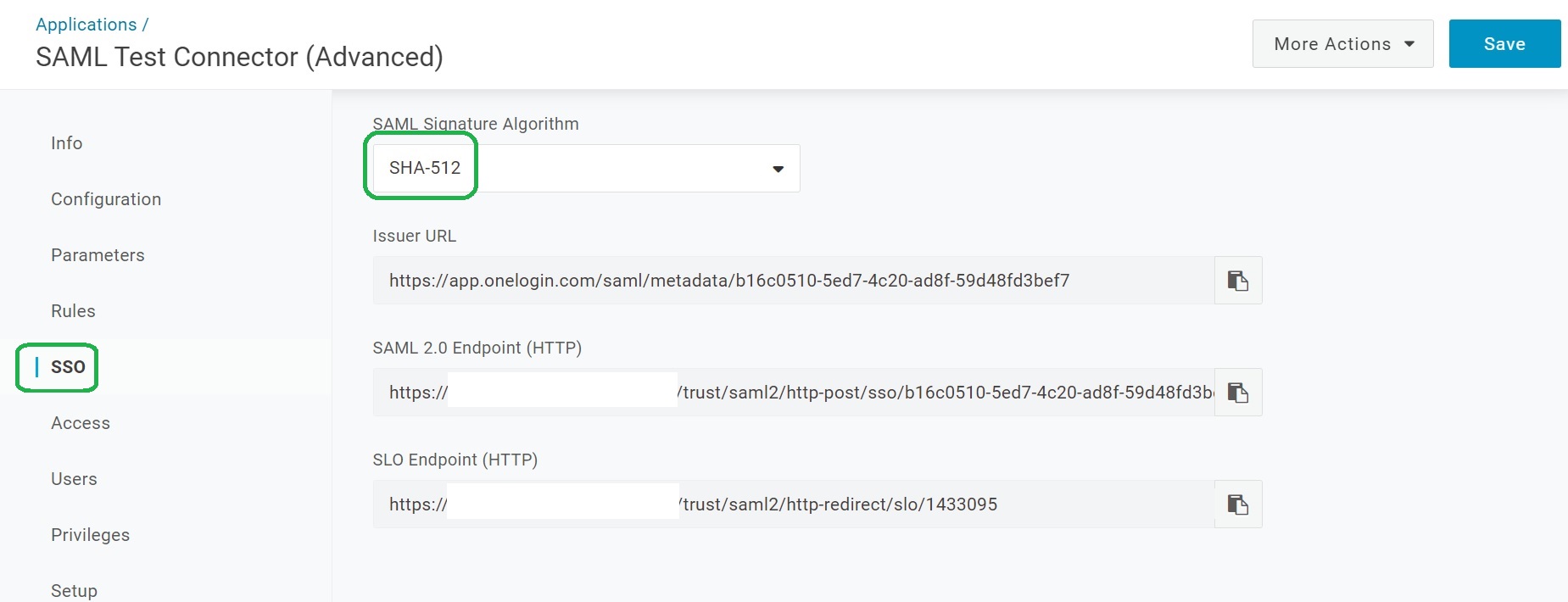
Configure SSO Settings
Open the SSO tab.
Set SAML Signature Algorithm to SHA-512 (SHA-1 is not secured for a signing).
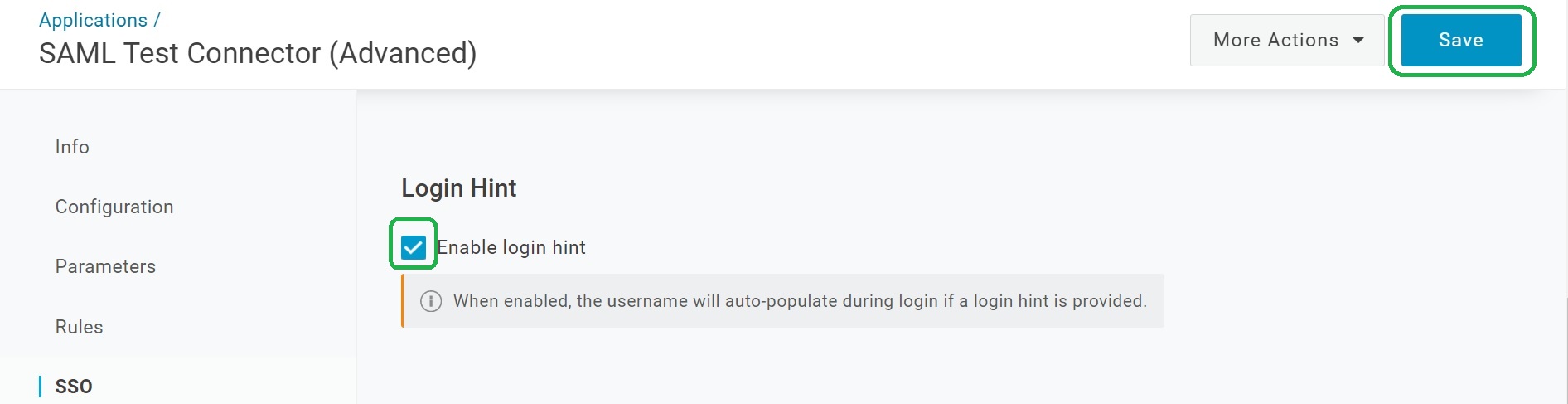
Uncheck Enable login hint and click Save.
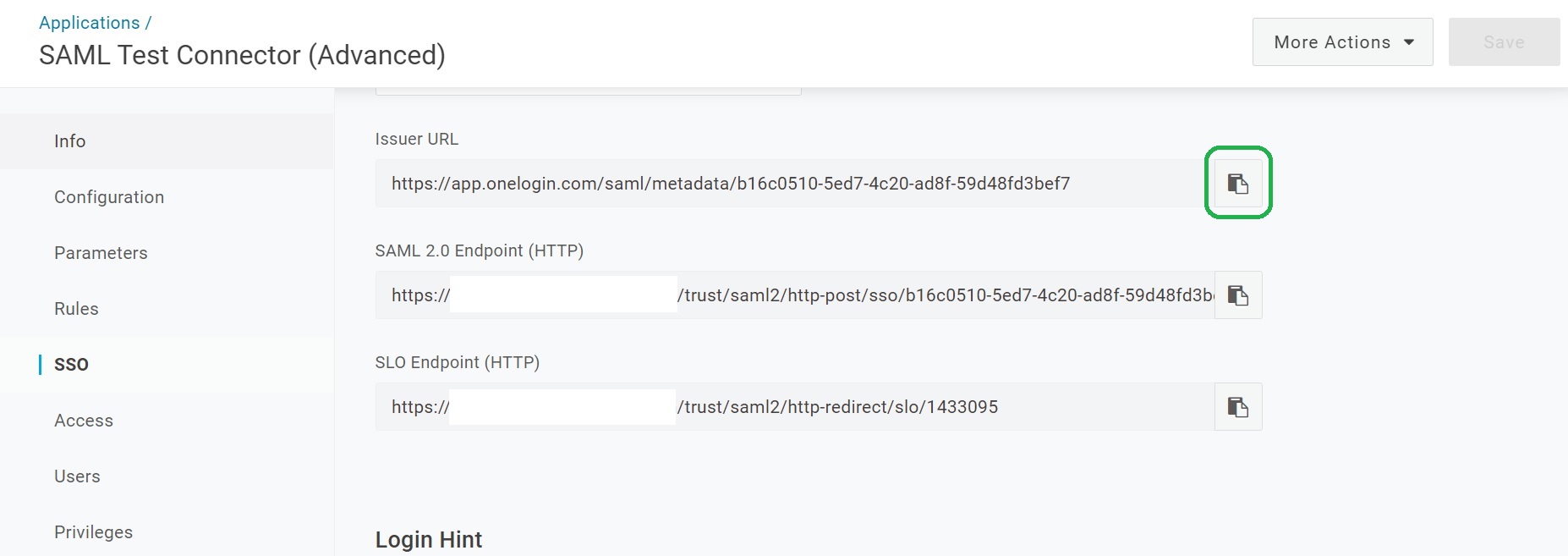
Copy the metadata link
Open the SSO tab.
Click on Copy To Clipboard of the Issuer URL setting.
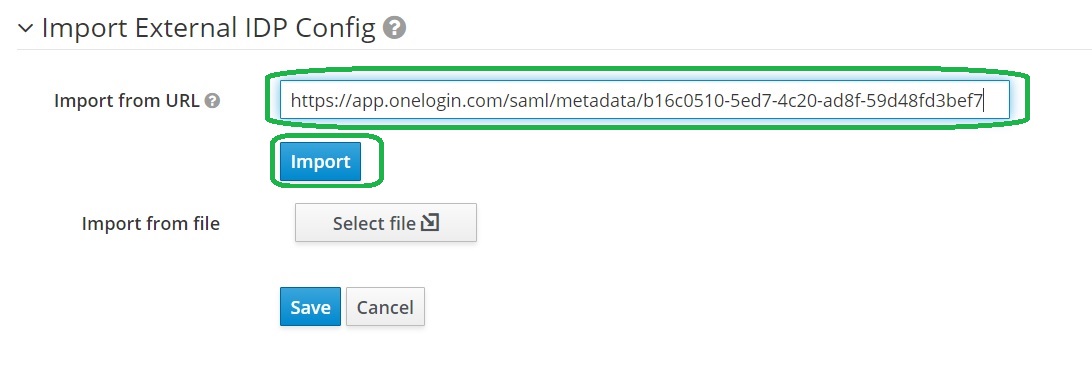
Import Onelogin Identity Provider Metadata into Keycloak
Open the Identity Providers configuration and paste the metadata link value into the Import from URL area and click the Import button.
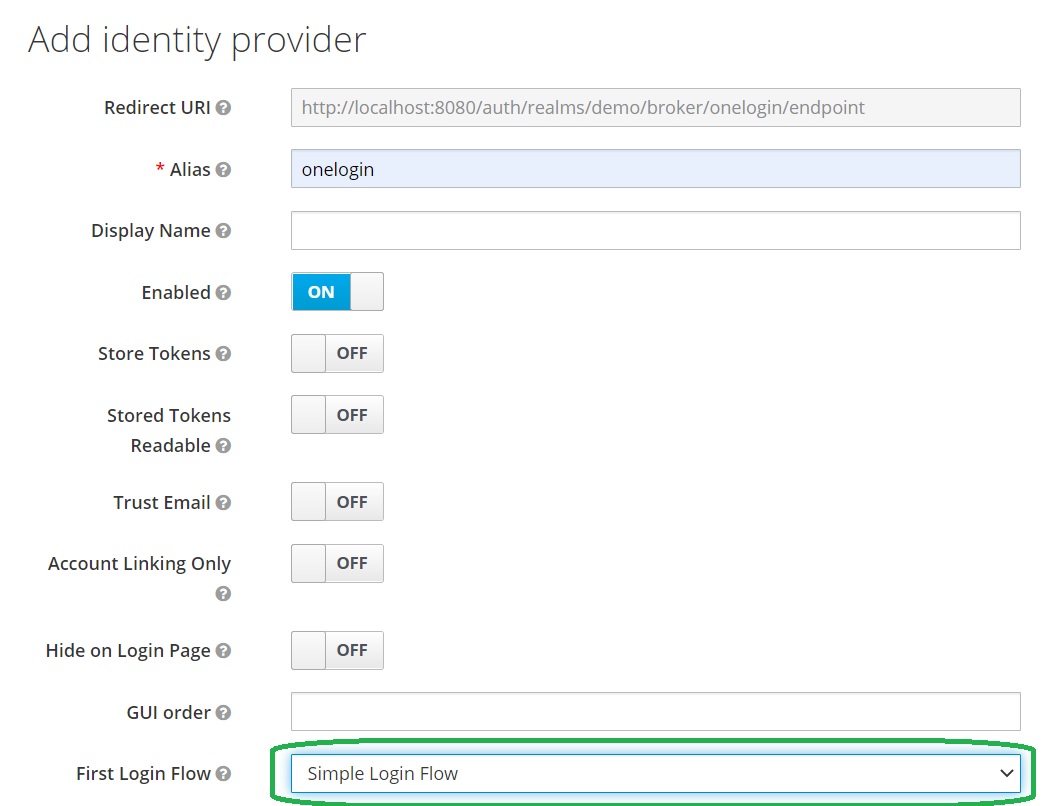
Configure First Login Flow
In my previous post I have described how to add Simple Keycloak First Login Flow
Let’s configure the flow. Select Simple Login Flow for the First Login Flow field.
Finally, save the provider configuration by click on the Save button.
Login using Onelogin SAML
You open the login page and you will surprise!
We have the additional button that allows us to login to Keycloak using the Onelogin SAML provider:
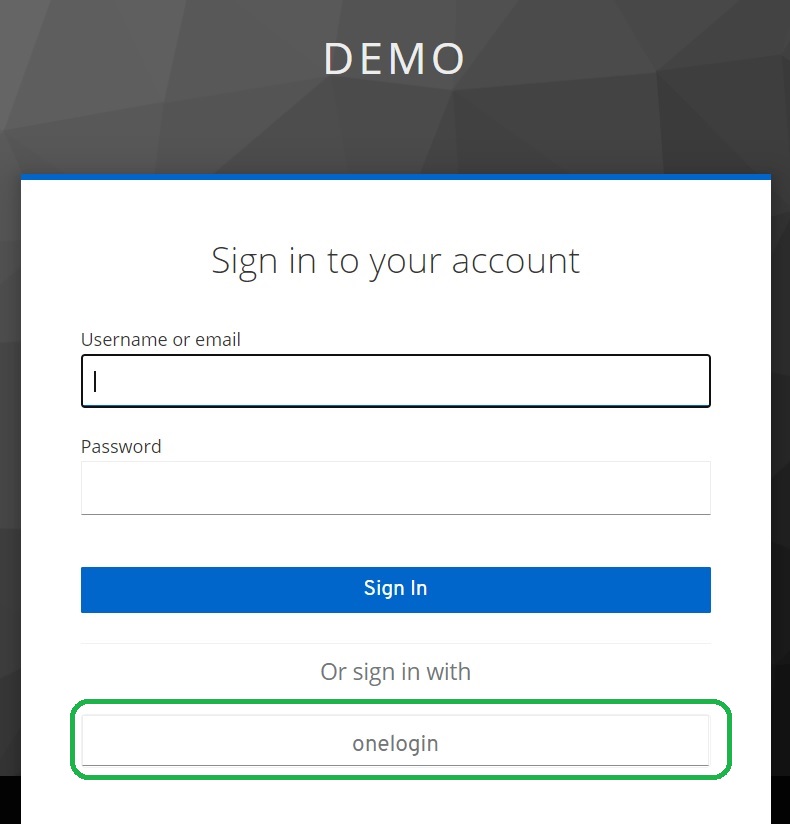
Note that you can configure Display Name in the provider configuration and to set more friendly name.
Click on the button and you will be redirected to the Onelogin SAML provider for the authentication.
After the successful authentication you will be redirected back to Keycloak.
Note: you need to assign users to the application.
Enjoy Onelogin SAML integration
Take-aways
You know how to integrate Keycloak with Onelogin SAML Provider
